A quick look at the CIA's Protego: likely a MANPADS missile control system
On 7 September WikiLeaks published several secret documents from the ‘Protego’ project of the CIA as part of their ‘Vault 7’ disclosures. Protego supposedly is a guided missile control system developed by Raytheon. The documents offer a rare public insight into classified missile control technology dated between 2014 and 2015. WikiLeaks claims it is a ‘suspected assassination module for GPS guided missile system’ ‘installed on-board a Pratt & Whitney aircraft (PWA) equipped with missile launch systems (air-to-air and/or air-to-ground)’, but i’m not so sure that’s what Protego actually is. Let’s take a look.
Protego Overview
Protego definitely seems to be a missile control system of some sort and consists of several micro-controllers that exchange data and signals over encrypted and authenticated channels as illustrated below:
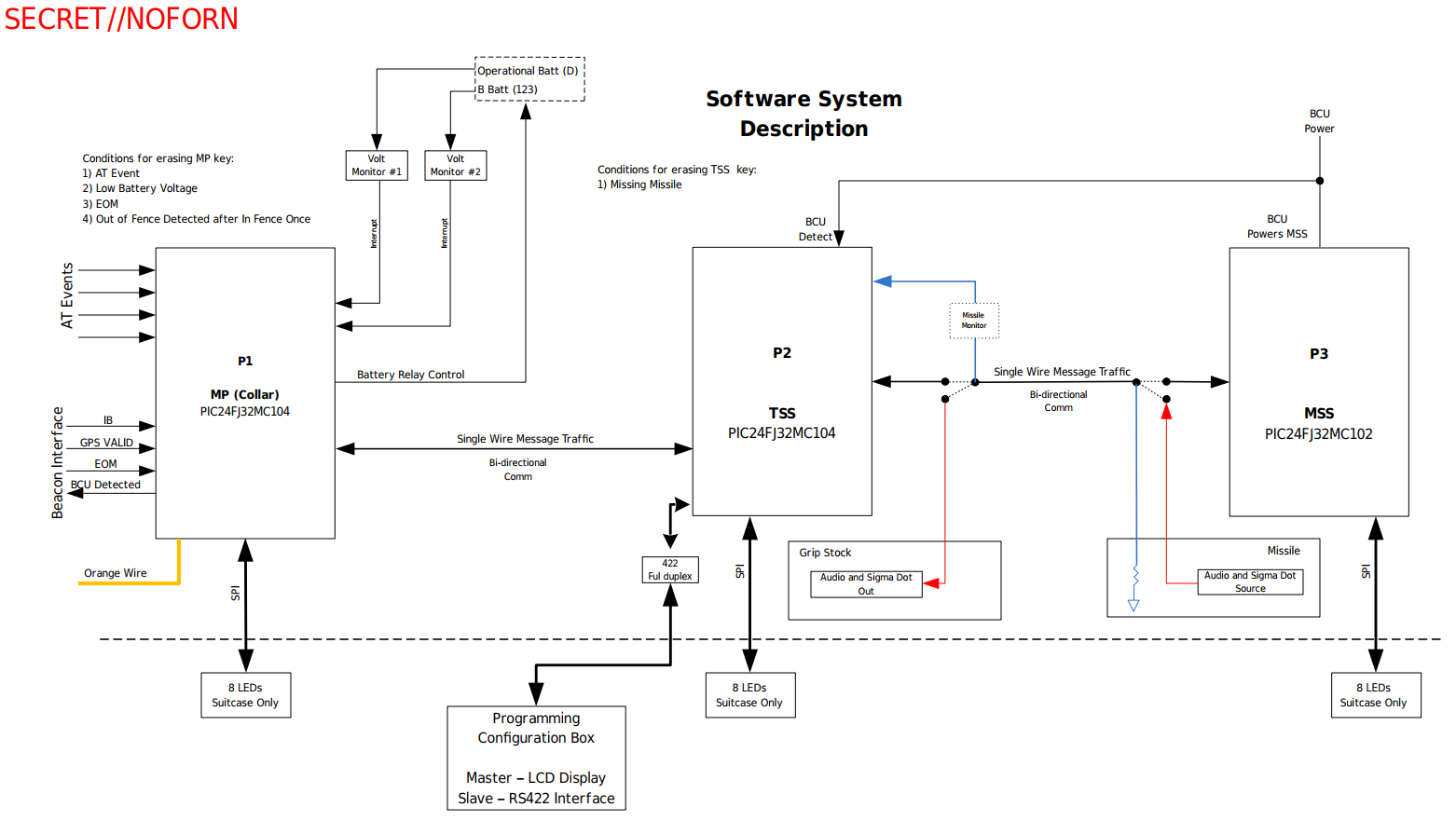
Some terminology might be helpful here:
-
Collar: The collar holds the missile before and at launch time and protects it against shock. See eg. this patent or the discussion on page 19 and onward here -
Tube: The launching tube from which the missile is fired. -
Missile: The actual missile itself.
The Protego components are as follows:
P1 MP (Collar)
The Master Processor (MP) consists of a master/slave model with P1 (master) and P1_S (slave). The MP consists of the low-cost, 16-bit PIC24FJ32MC104 micro-controller intended for motor control applications, which features a Modified Harvard architecture, a 16-bit-wide data path, 32 Kbytes of flash program memory and 2 Kbytes of data SRAM.
The MP has the following interfaces of interest:
-
AT Events: The nature of this interface is unclear its incoming signals seem to be a condition for erasing theMPkey. Possibly stands for anti-tampering. -
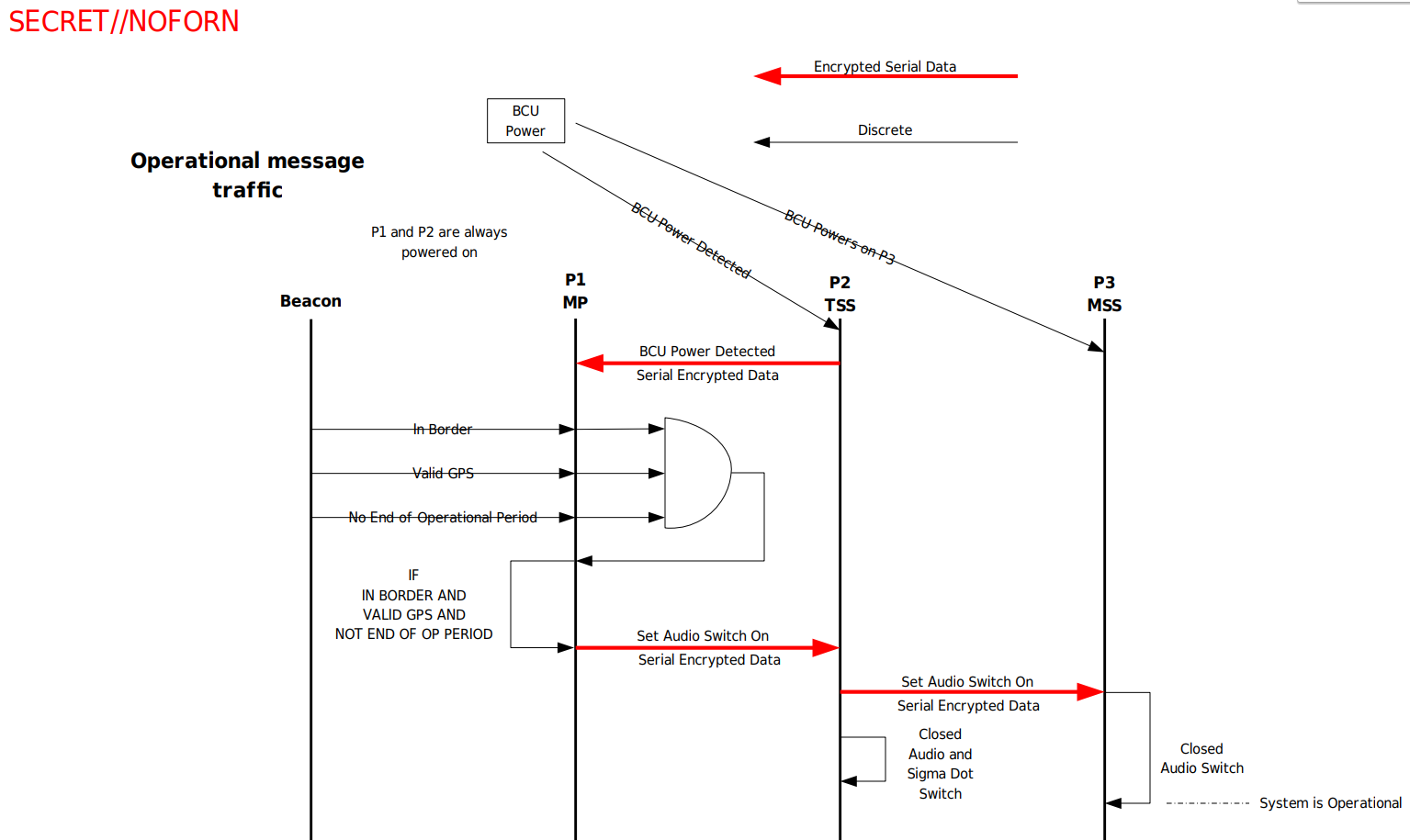
Beacon Interface: This interface has three incoming signals:IB(In Border),GPS VALID,EOM(No End of Operation Period). The first signals whether the aircraft is within the defined area of operation, the second whether a valid GPS signal is available and the third whether the current time is within the defined operational timeframe. As shown in the figure below, missiles are only launched if all these signals are set to true. This interface has only one outgoing signal namedBCU Detected. TheBCU (Battery Coolant Unit)is used for the targeting system, missile powering and cooling detectors before launch. The outgoingBCU Detectedsignal simply transmits the one received and passed on by theTSSto theMPover the bi-directional comm. -
Bi-Directional Comm: This is a bi-directional single-wire message traffic interface between theMPandTSSfor encrypted serial data.
P2 TSS
The Tube Smart Switch (TSS) also consists of a PIC24FJ32MC104 micro-controller. The TSS has the following interfaces of interest:
-
422 Full duplex: ARS-422serial interface with theDeployment / Programming Box. -
BCU Detect: TheBCUdetect signal indicatingBCUhas been inserted. -
Bi-Directional Comm (1): This is a bi-directional single-wire message traffic interface between theTSSandMSSfor encrypted serial data. Note that this interface is connected to a grip stock and the missile and providesaudioandsigma dotout signals. In missile control engineering,sigma dotrefers to the line of sight rate. -
Bi-Directional Comm (2): This is a bi-directional single-wire message traffic interface between theTSSandMPfor encrypted serial data.
P3 MSS
The Missile Smart Switch (MSS) consists of the PIC24FJ32MC102 micro-controller which has similar specs to the PIC24FJ32MC104. The MSS has the following interfaces of interest:
-
BCU Power: TheBCUpowers on theMSS. -
Bi-Directional Comm: This is a bi-directional single-wire message traffic interface between theTSSandMSSfor encrypted serial data.
P4 & P5 Deployment / Programming Box
The Programming / Configuration Box, also called the Deployment Box, consists of a Master P5 micro-controller handling the LCD display and Slave P4 micro-controller handling the RS422 interface with the TSS.
Protego Functionality
Programming / Deployment
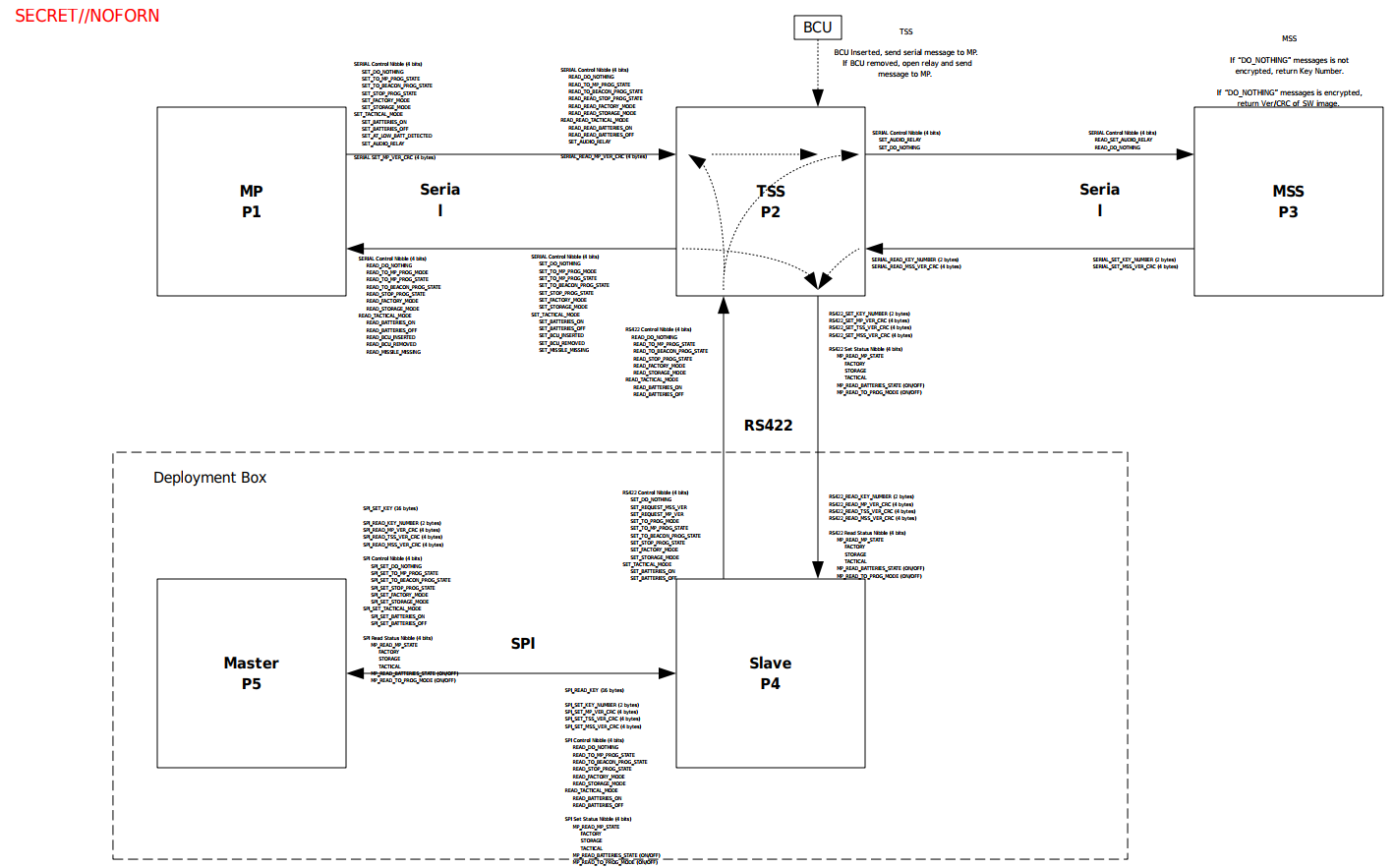
According to the Protego build procedure document, build images are generated with a corresponding key. Eg. for key number 3002 we get image 3002_P1.X.production.hex for the MP master micro-controller image. Not all micro-controllers contain keys, only MP, TSS and MSS do with the deployment box images being keyless. Beside references to the Protego keys (numbers starting at 2000), there is also a reference to Devil Snare keys (numbers starting at 1000), likely a separate but related system. These keys are generated by a dedicated KeyGen application on a host workstation computer and written into the images during build.
For reprogramming the MP master processor, the P1_S.X (P1 Slave) (the MP slave image) and maintenance image P2_Maintenace (the TSS reprogramming image) are created using an engineering maintenance key located within the images which are used on any Protego system, regardless of key, to reprogram the MP master processor.
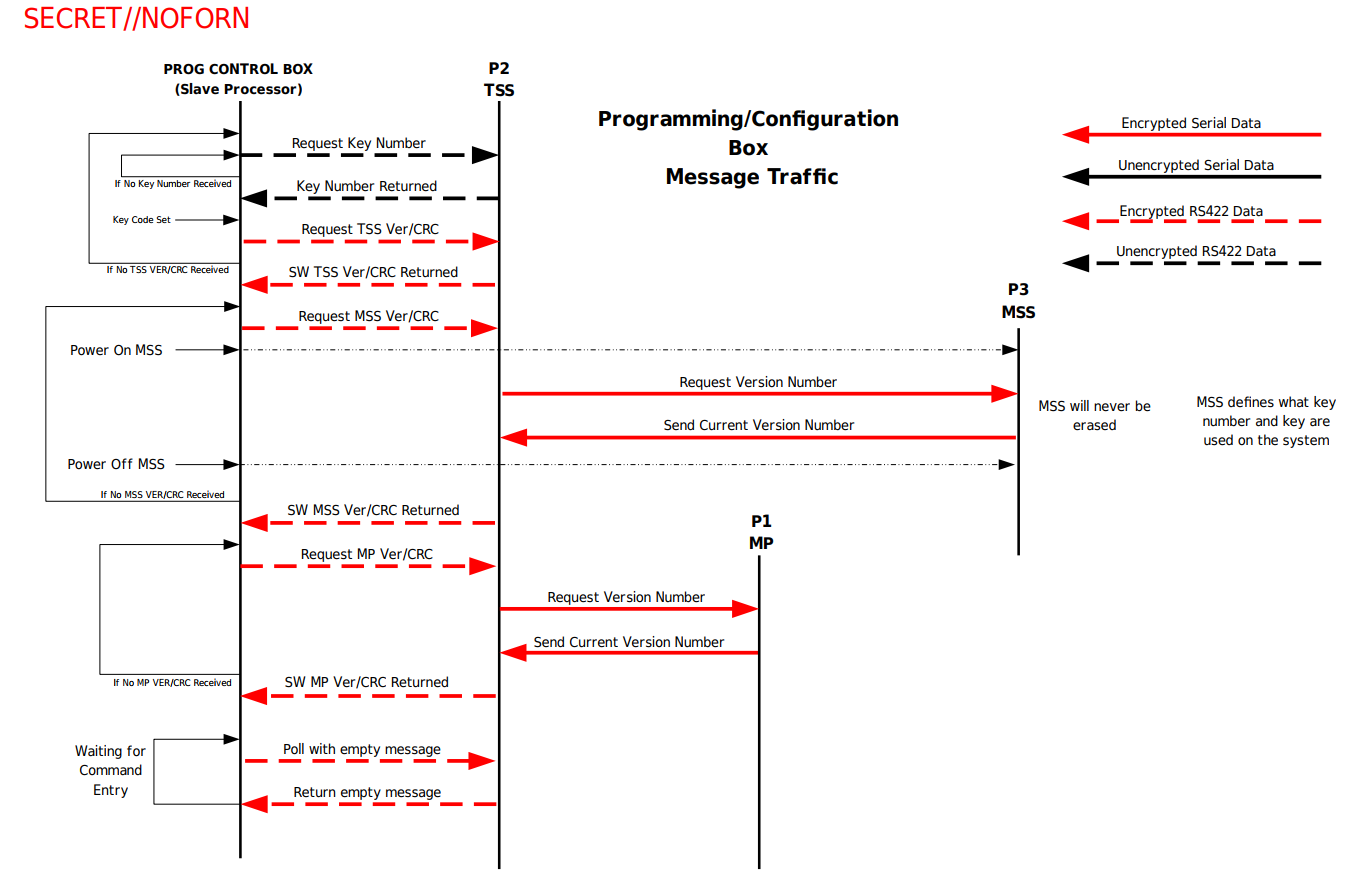
As shown in the picture above, the Programming / Control Box requests (in plaintext) a key number from the TSS and after it’s received one continues communicating in ciphertext (presumably using the key corresponding to the key number the TSS sent). My suspicion is that all keys are shared symmetric keys here. Looking at the following image lifted from one of the documents:
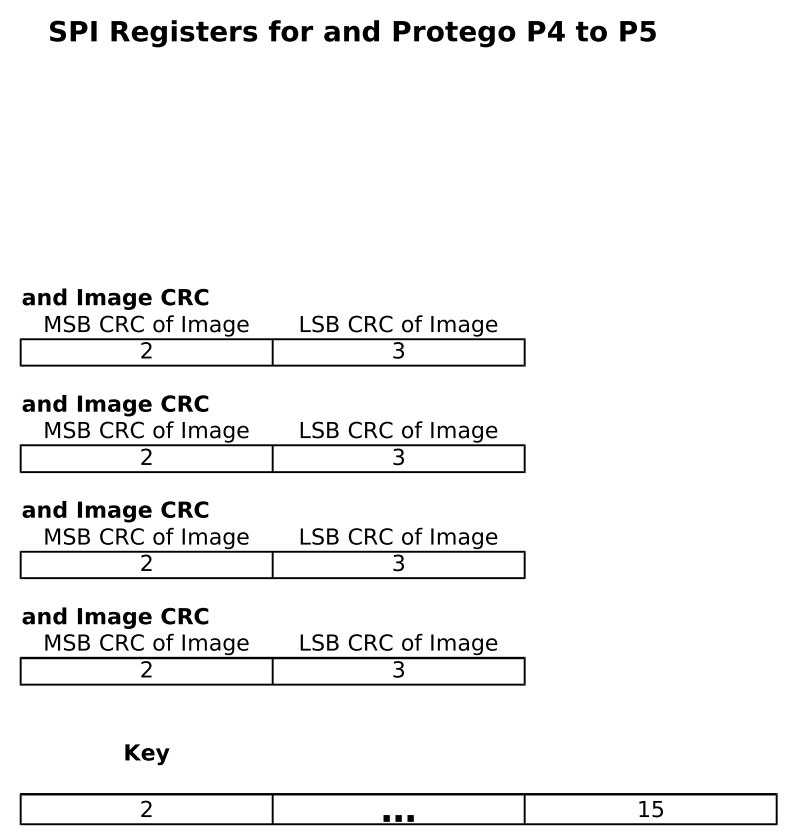
We can see the key is 14 bytes or 112 bits long, which could correspond to something like the 2TDEA Triple DES keying option, but there’s really no way to tell. Either way, the programming box continues to request TSS, MSS and MP versions and 16-bit image CRCs.
Given the functional activities listed in the programming / deployment box (eg. SPI_SET_KEY, SPI_SET_TACTICAL_MODE, SPI_SET_STORAGE_MODE) and the fact that it apparently has an LCD display i assume this allows for in-field programming provided the right keys are entered (since none are stored on the programming / deployment box itself).
Key Erasure
As pictured below, Protego supports auto-destruction of keying material when certain conditions are met:
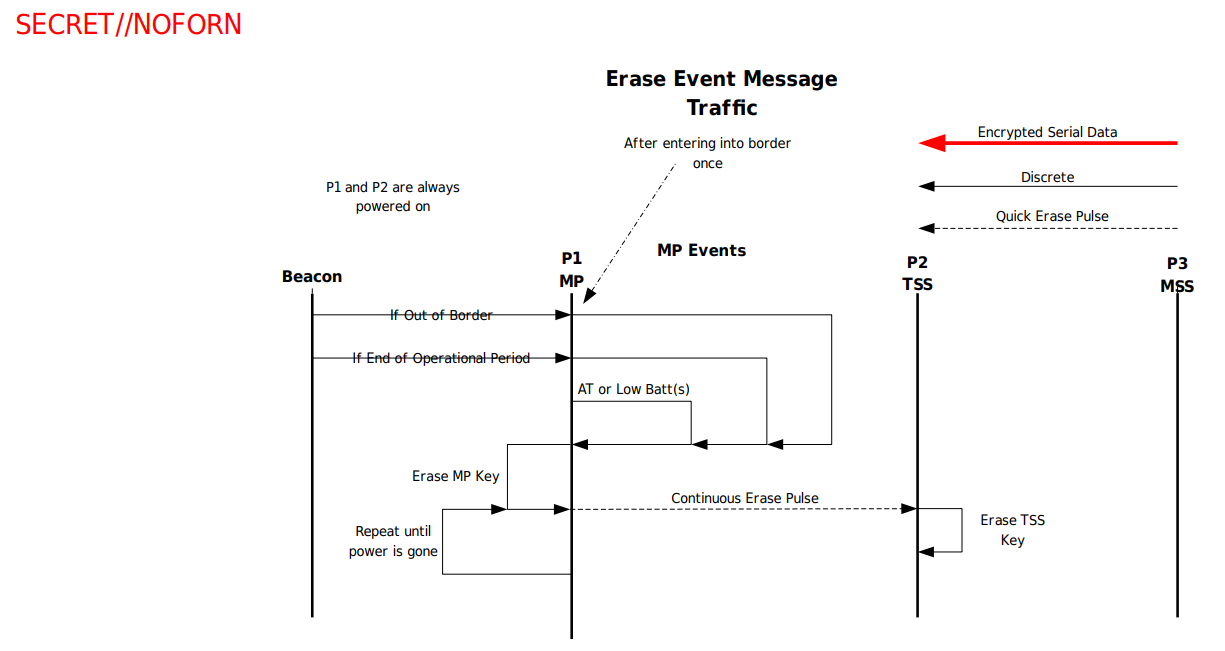
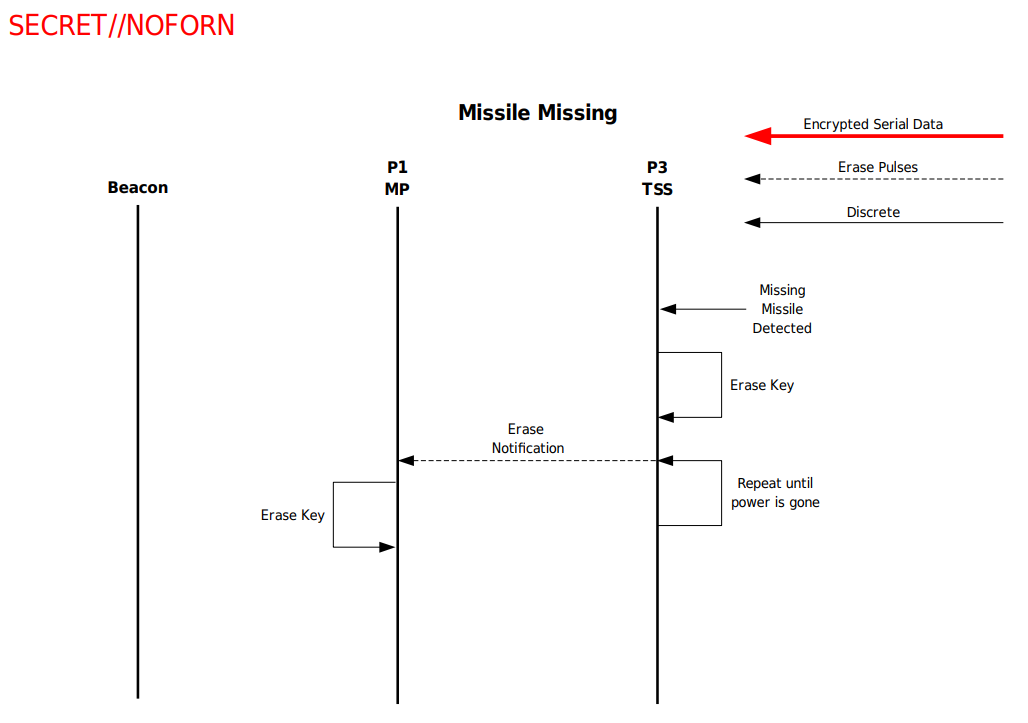
The conditions include:
- AT events being triggered
- A low battery voltage
- The end of the operational period
- Out of Border being detected after being within the Border once
- Missile missing
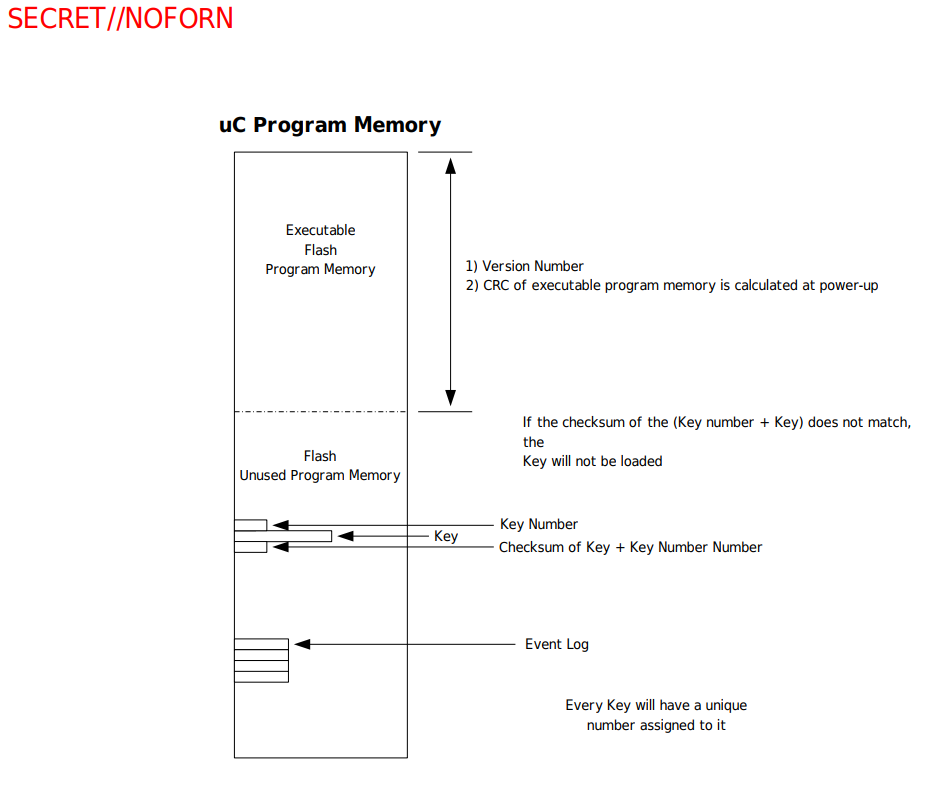
Key Verification
As shown in the image below, the CRC of the program executable is generated at power-up and a checksum of the key number + key is determined and checked before loading the key. For the sake of Protego, i hope that’s a cryptographically secure checksum and not a CRC (not that it matters that much with the seeming lack of any secure boot / firmware integrity verification).
So what exactly is Protego?
First of all, the name seems to be a reference to a shield charm in Harry Potter much like the referenced Devil Snare seems to be a reference to a magically constricting plant in the same Harry Potter universe.
WikiLeaks claims Protego is a ‘suspected assassination module for GPS guided missile system’ ‘installed on-board a Pratt & Whitney aircraft (PWA) equipped with missile launch systems (air-to-air and/or air-to-ground)’ but this seems to make less and less sense the more you look at the documents. First of all, without further context, the only reference to Pratt & Whitney aircraft seems to be based on deducing this from the PWA acronym in the building procedure document. Besides, it seems Pratt & Whitney aircraft mostly manufactures aircraft engines which seems like a weird fit for ‘installing a missile control system’ onto to say the least.
Secondly, while i’m by no means an expert on military technology there are references to components that seem out of place for air-to-air (AAM) or air-to-surface/ground (ASM/AGM) missiles such as mentions of a grip stock, BCU and its insertion and a suitcase with LEDs:
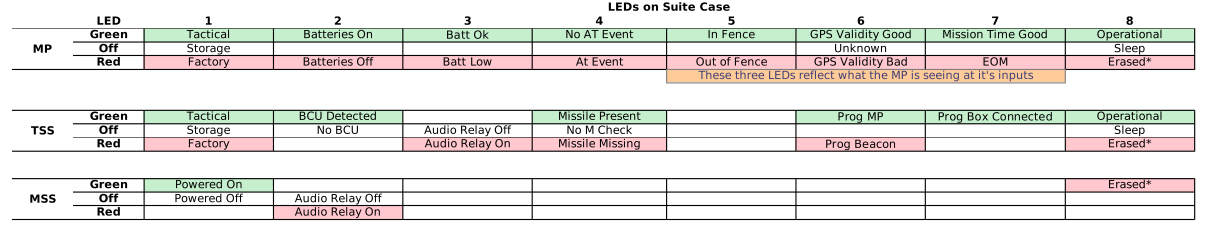
It seems that it is far more likely that Protego is a missile control system for controlling MANPADS such as the
FIM-92 Stinger which have a grip stock, have a BCU inserted into the handguard that shoots a stream of argon gas and a chemical energy charge into the system to provide power and cooling as shown below:

Such MANPADS come in large suitcases which could be outfitted with status LEDs on the outside:

Unless clear documents are forthcoming, there is no way to know for sure, but i suspect Protego might be intended to enforce a degree of control over MANPADS used by less-than-trusted third parties. The terminology of a ‘smart switch’ used throughout the documents, the functionality of Protego which consists effectively of geo-fencing and ‘time fencing’ usage of the missile launch system to a specific geographical area and operational period of time and the necessity of having key material to put the system in factory test, storage or tactical mode (the latter presumably being the only one in which it can fire) all hint at this. There also seems to be an event-log stored in micro-controller program memory, possibly to aid in forensics in the event of tampering or recovery after theft/unauthorized use.
And it makes even more sense if you think about the reason why the CIA would need such a system, especially one using deniable commercial off-the-shelf (COTS) non-MILSPEC components such as the PIC microcontrollers. After all, there have been continuous media reports of Syrian rebel groups being supported by covert CIA programs with a persistent worry being exactly an uncontrolled proliferation of US-supplied MANPADS. Overt US efforts to keep MANPADS out of the conflict not withstanding, reports have mentioned the desire to design safer MANPADS for Syrian rebels:
In recent days, U.S. officials have hinted that they may be willing to provide the weapons — known in military circles as MANPADS, short for “man-portable air defense system” — with one major caveat: They include technical controls that would limit where they can be used to ensure they don’t one day fall into terrorist hands.
But the design of such weapons controls remain highly elusive. U.S. engineers aren’t known to have sorted out how to build a GPS chip into the weapon that would ensure it could be fired only on the front lines of northwest Syria. They also haven’t sorted out a way of rendering the weapons inert after a certain amount of time so they don’t show up on distant battlefields way in the future. Weapons can be hacked, and arms control experts fear MANPADS supplied by the United States might end up with militants from groups like the Islamic State, reconfigured, and then used to shoot down a civilian airliner.
It’s possible that CIA engineers have secretly built and tested MANPADS and are waiting for the right moment to deploy them. If so, the agency has remained mum. The CIA declined to comment for this article. Raytheon, which makes the primary MANPADS in the American arsenal, the Stinger, declined to comment. The Pentagon referred comment to the State Department, which declined to comment on reports of MANPADS being delivered to Syria.
If you ask me, this sounds a whole lot like Protego (including the geo-fencing, CIA and Raytheon mentions). Considering the names (Protego and Devil Snare) and their association with protection, shielding, ensnaring and constriction this seems like a good fit as well. The Devil Snare system might very well be a secondary component handling, for example, the verification of GPS data and geo- and time-fencing operations incoming on the beacon interface.
Of course, all of this is just wild speculation but it seems like a better fit than the original WikiLeaks suggestion of being an aircraft-based missile control system.
samvartaka 08 September 2017